Versions Tested:
Web Revision: 1.107, Board: 3.001, Firmware: 2.213
Security Advisories:
N/A
CVE Numbers:
CVE-2020-11542
CVSS Score:
N/A
CWE:
CWE-305: Authentication Bypass by Primary Weakness
NIST:
IA-4: Identifier Management
OWASP:
A2: Broken Authentication
With access to a system’s control interface, a malicious actor can unlock controls remotely, allowing them to gain physical entry to restricted areas. However, lessons learned from other breaches can help everyone better understand how to prevent unwanted access.
During an internal penetration test, our team discovered a physical access control system from Infinias on the target network. As luck would have it, the device was still configured with default credentials, which allowed us to log in and look around. After briefly browsing the manufacturer’s site and reading their documentation, it became clear that this could be an interesting target as the Infinias eIDC is a PoE-enabled door controller that allows one or more physical access control systems to be integrated into a network for ease of management. It was interesting to find a device configured to still accept default credentials. However, we did notice something else that was strange. When reviewing HTTP logs in Burp Suite, the string “CMD” was found in a number of requests. That sounded juicy, so we did what red teamers do and started chasing the white rabbit down a hole.
We discovered that the Infinias eIDC32 WebServer has an exploitable authentication bypass vulnerability due to unsecure authentication methods handled on the client-side JavaScript. This would have been more difficult to identify without a set of valid credentials, whether default or not. However, with physical access to IoT devices like these, the firmware can be pulled off and analyzed to take an even deeper dive.
Technical Details:
Greeted with the device’s web interface we were able to log in using default credentials found within their documentation.

While watching the traffic in Burp Suite, this little gem stood out immediately.

When intercepted, this is the HTTP Response to the request with valid credentials:

At this point, we decided to take a look at the source code to see how the authentication was being handled. A quick search for the string “LGI” returned the following bit of vulnerable code:
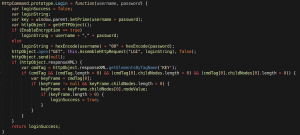
This section simply hex encodes the username/password and adds a “00” between the two encoded values. The next step was to start digging in to see the differences between valid and invalid credentials. Submitting another authentication request with invalid credentials (UN:AAAA PW:AAAA) confirmed this.
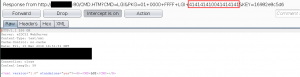
Comparing the HTTP responses of invalid and valid credentials, the difference becomes clear. The HTTP response to the successful login contains the string “<KEY>MYKEY</KEY>” in the XML body data, whereas the failed login does not.
Using Burp Suite, we intercepted the eIDC32 WebServer’s response to our login attempt using invalid credentials. From there, we added the string “<KEY>MYKEY</KEY>” to the XML body data to match the successful login response and forwarded the response.
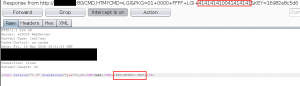
Changing this value in the HTTP response bypasses the client-side JavaScript controls, allowing an attacker with invalid credentials to bypass the login process of the device and access it as an administrative user.
Lessons learned
While central management of networked access control systems can be a huge convenience, it is important to ensure that the systems are configured properly, kept updated, and to disable/change any default accounts to prevent malicious activity.
Timeline:
3/20/2019 – First communication sent to the vendor
3/22/2019 – Technical Support replies saying it will be sent to the “access team” for review
3/25/2019 – Response from a second technical support employee:
“What vulnerability are you speaking of? We do get flagged on occasion for different things. To my knowledge, most or all have a workaround”
3/25/2019 – Back and forth discussing finding, submitted PDF with additional details, no response.
4/8/2019 – Still no response, I reached back out to no avail.
9/30/2019 – The client met with a rep from Stanley Security, 3XLogic’s parent company, and connected us. All info including the write-up and previous emails were sent to Stanley Security.
2/27/2020 – No response still
3/12/2020 – Submitted for CVE
Credit:
Discovered by the following Security Researchers for TEAMARES at CRITICALSTART
Quentin Rhoads-Herrera, Director of Professional Services – @paragonsec
Cory Mathews, Offensive Security Manager – @M3chSec
Chase Dardaman, Senior Adversarial Engineer – @CharlesDardaman
New course offered at BlackHat 2020:
To help sharpen the skills of penetration testers and threat hunting teams, TEAMARES will be offering an onsite training course at BlackHat USA 2020 in “Adversary Emulation and Active Defense.” This course will provide information security concepts utilized in both offense and defense. Attendees will learn skills that can be applied to increase capability from both sides including exploitation, circumventing defenses and lateral movement from an attacker’s perspective. The course will also cover key techniques for detection, threat hunting and mitigation to counter an attacker’s toolbox.
Follow us on Twitter @TeamAresSec and @CRITICALSTART to stay up to date on vulnerability discoveries and cybersecurity news.




