
When TEAMARES began research into the vulnerability identified in the F5 TMUI RCE vulnerability advisory released last month, we initially started by reading the advisory and mitigation steps, which contained minimal details but included key pieces of information needed to kick off our research. The advisory states that the vulnerability impacts a variety of capabilities when exploited, including the ability to execute arbitrary Java code, which stood out to us.

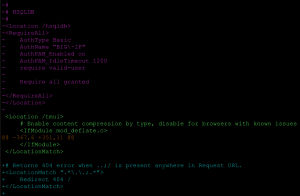
Reading the mitigation steps immediately points to directory traversal and potential command injection. The interesting character in the pattern is the semicolon.
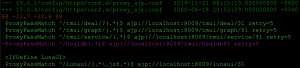
The first step was to compare changes between the known vulnerable versions and the fixed versions, so we began by comparing system configurations between 15.1.0 against 15.1.0.4. We found that there were a plethora of differences, but the following changes to the Apache configuration piqued our interest in particular and led to us going down this rabbit hole.
The screenshots show the /hsqldb endpoint was removed from the reverse proxy configuration. The Tomcat application server listens on localhost:8009.
Running a basic unauthenticated GET request redirected to the login page, which is expected as authentication is required to access the management application.
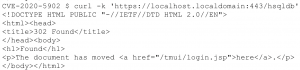
With the vulnerability mitigation steps in mind, we appended a semicolon and the request was successfully sent to the application server. This must be the authentication bypass because this endpoint should not be reachable.
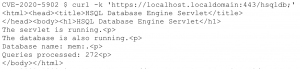
Now that we could reach /hsqldb, we set off on a journey to see what could be done with it. HyperSQL is an embedded relational database used by Java applications. Through reading documentation and looking for ways, this could be abused.
The first attempt used a User Defined Function (UDF); however, it was discovered that the feature is not available in v1.8. We found that we could call native Java functions or any method available to the server with the primary restriction being that it had to be a static method. After looking for static methods in the HSQLDB source code, we found the org.hsqldb.util.ScriptTool.main() method deserializes a Java objected represented as an ASCII hex string. This looked very promising, so we attempted to call this manually using sqltool and hit a “Serialization failure” error.

Thankfully, the error message informed us of how to resolve it. Setting the enableUnsafeSerialization property to true and executing the payload was successful. At this point, we proved that authenticated remote code execution was possible. Attempting to use /hsqldb; with a POST request resulted in a connection error, so we took another look at the mitigation regex “.*\.\.;.*” and noticed that the authentication bypass was “..;”. We then changed our exploit to work with that regex, allowing us direct access to HQSLDB.
The full exploit which can be found at https://github.com/Critical-Start/Team-Ares/tree/master/CVE-2020-5902.
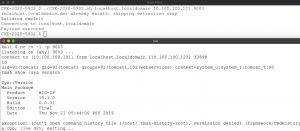
Create a new user with the admin role via tmsh. This operation creates a root system account.

Versions Tested:
- F5 BIG-IP 15.1.0
- F5 BIG-IP 14.0.0
References:
- https://support.f5.com/csp/article/K52145254
- https://www.ptsecurity.com/ww-en/about/news/f5-fixes-critical-vulnerability-discovered-by-positive-technologies-in-big-ip-application-delivery-controller/
Credit:
Authentication bypass discovered by Mikhail Klyuchnikov of Positive Technologies
Proof of Concept research by Charles Dardaman, Senior Adversarial Engineer, and Rich Mirch, Senior Adversarial Engineer for at CRITICALSTART, TEAMARES




