
Version Tested:
3.0.0
Product:
https://www.opsramp.com/
CVE Numbers:
CVE-2020-11543
CVSS Score:
10.0 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
CWE:
CWE-798: Use of Hard-coded Credentials
OWASP:
https://owasp.org/www-community/vulnerabilities/Use_of_hard-coded_password
Summary:
During a recent penetration test, CRITICALSTART‘s TEAMARES researchers discovered that OpsRamp Gateway has an administrative account named vadmin that allows root SSH access to the server. This account was unknown to clients unless requested through a support process. At that time the vendor states they would provide the account to the client and request that they change the password.
Prior to the patch, this password was not unique to all clients, only to those who requested access to the account and changed the password. Critical Start is unaware of the number of clients that may have requested access and changed the password.
Technical Details:
After installing the OpsRamp Gateway server, a script called “kick-start.sh” runs, which sets up multiple user accounts and hardcodes their passwords by setting the pre-hashed passwords.
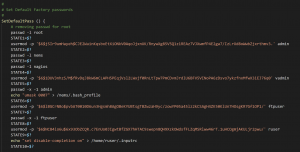
Our team was able to crack the hash for the vadmin, which can be used to SSH into the server with the password 9vt@f3Vt. Additionally, the account has the sudo permissions ALL, allowing us to easily escalate to root with sudo -i.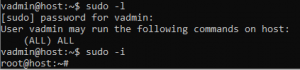
We then proceeded to log into client servers in production as root proving that the hashes are not unique to the install.
Timeline:
10/24/2019 – Vulnerability found
01/20/2020 – CRITICALSTART was informed that the Vendor patched the finding
03/26/2020 – Ensured that clients were patched
03/26/2020 – CVE Requested
04/07/2020 – Released vulnerability disclosure
Credit:
Discovered by Charles Dardaman, Senior Adversarial Engineer for TEAMARES at CRITICALSTART
Our Team:
CRITICALSTART’s TEAMARES is comprised of professionals with more than a decade of experience conducting offensive and defensive security services. Our team has expertise in a wide array of industries, including oil and gas, healthcare, app development firms, hospitality, technology, and more.
Follow us on Twitter @TeamAresSec and @CRITICALSTART to stay up to date on vulnerability discoveries and cybersecurity news.




