Data shows the number of alerts is up, longer times to investigate and high false-positive rates
PLANO, TX – August 29, 2019 – CRITICALSTART, a leading provider of Managed Detection and Response (MDR) services, today published new research revealing that Security Operations Center (SOC) analysts continue to face an overwhelming number of alerts each day that are taking longer to investigate, leading five times as many SOC analysts this year to believe their primary job responsibility is simply to “reduce the time it takes to investigate alerts.” The most striking finding is the direct toll the alert overload problem is having on SOC analysts with more than 8 out of 10 reporting that their SOC had experienced at least 10% up to more than 50% analyst churn in the past year.
CRITICALSTART’s second annual report – The Impact of Security Alert Overload – surveyed SOC professionals across enterprises, Managed Security Services Providers (MSSP) and Managed Detection & Response (MDR) providers to evaluate the state of incident response within SOCs from a variety of perspectives, including alert volume and management, business models, customer communications as well as SOC analyst training and turnover.
Key findings from the 2019 report include:
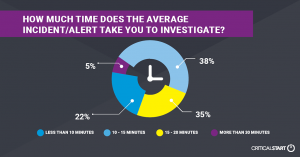
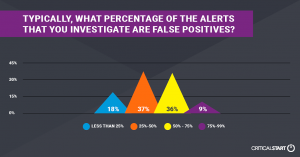
- Alert Overload: 70% of respondents investigate 10+ alerts each day (up from 45% last year) while 78% state that it takes 10+ minutes to investigate each alert (up from 64% last year). In addition, false-positives remain a struggle, with nearly half of respondents reporting a false-positive rate of 50% or higher, almost identical to last year.
- Response to Alert Overload & Main Job Responsibility: with the onslaught of alerts, 38% of respondents say their SOC either tries to hire more analysts or turn off high-volume alerting features deemed too noisy, both up significantly from last year. The number of respondents that feel their main job responsibility is to analyze and remediate security threats has dropped dramatically from 70% down to 41% as analysts increasingly believe their role is to reduce alert investigation time or the volume of alerts.
- Customer Transparency & Communications: A clear majority of respondents (57%) report that MSSPs and MDRs offer limited to no transparency for customers into investigations or underlying data. And in the age of the mobile enterprise, email is still king for customer communications – 73% of respondents report interacting with customers via email, followed by 47% via a desktop portal.
- Annual Training: Nearly half of respondents say they get 20 or fewer hours of training per year, a surprise given today’s dynamic threat environment.
- SOC Analyst Turnover: In the past year, 80% of respondents report SOC turnover of more than 10% of analysts, with nearly half reporting a 10-25% turnover.
“The research reflects what we are seeing in the industry – as SOCs get overwhelmed with alerts, they begin to ignore low to medium priority alerts, turn off or tune out noisy security applications, and try to hire more bodies in a futile attempt to keep up,” said Rob Davis, CEO at CRITICALSTART. “Combine that stressful work environment with no training and it becomes clear why SOC analyst churn rates are so high, which only results in enterprises being more exposed to risk and security threats.”
About CRITICALSTART
CRITICALSTART, the MDR experts that leave nothing to chance. The company developed the industry’s only cloud-based, SOAR platform that resolves 99% of security events on its own to eliminate compromises and stop breaches. Our mission is simple: protect our customers’ brand while reducing their risk. We do this for enterprises through our award-winning portfolio of end-to-end security services, including MDR and Professional Services. Visit www.criticalstart.com for more information.
###




