Managed Detection & Response
At CRITICALSTART, we leave nothing to chance. Our Managed Detection and Response platform is built to efficiently detect and resolve every alert. By adapting to the unique processes and requirements of your business, our MDR services reduce attacker dwell time and stop breaches.
Our Approach
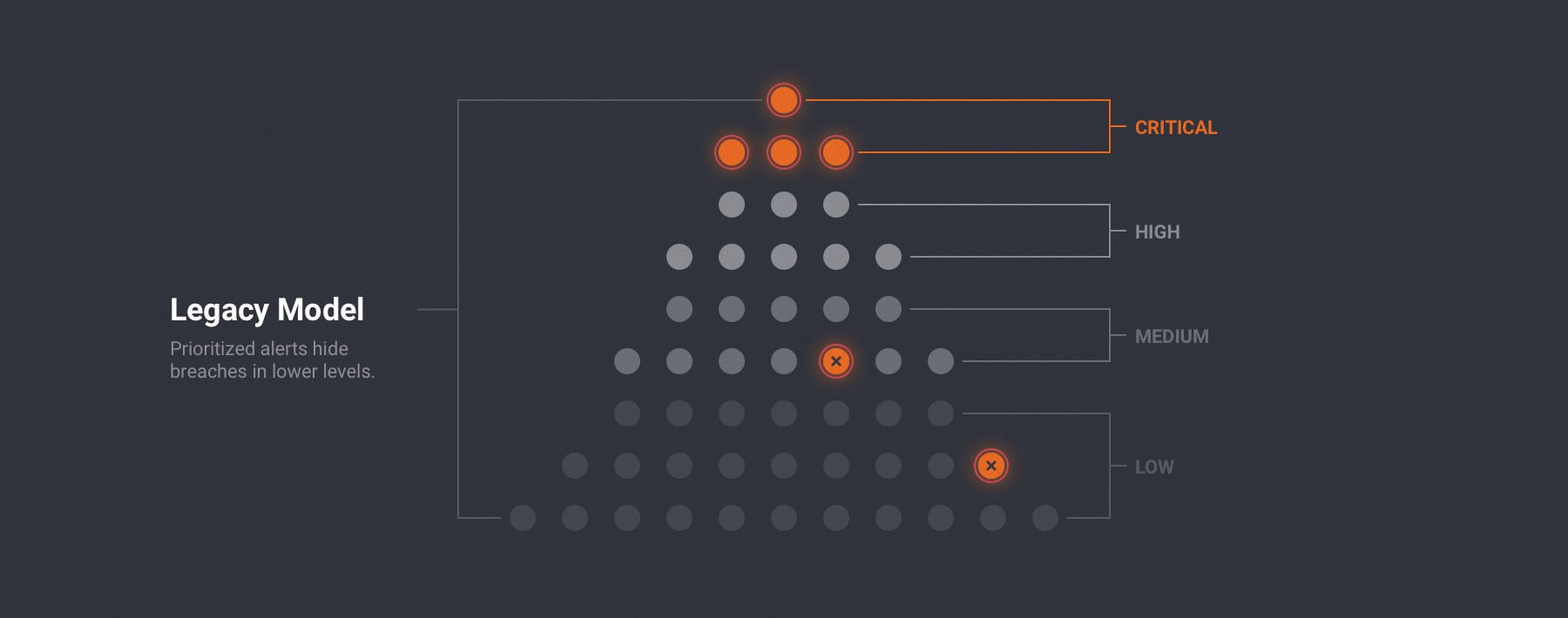
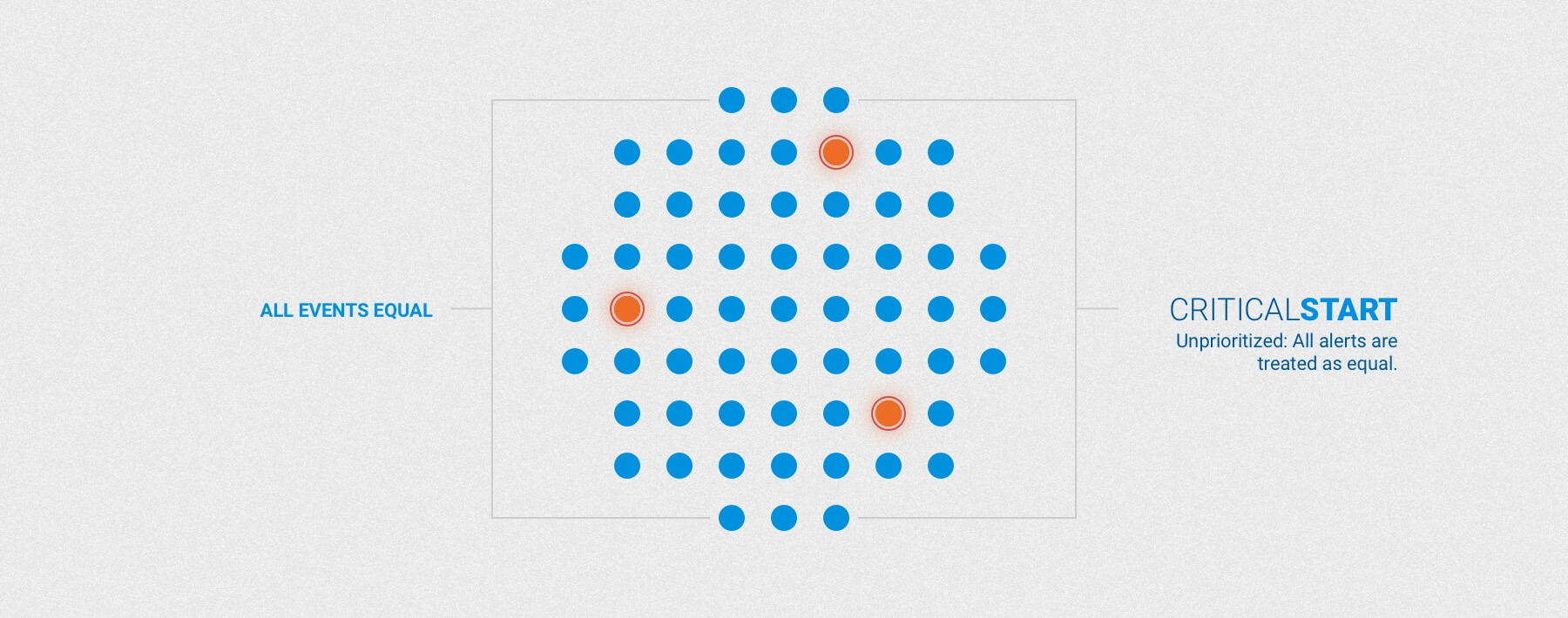
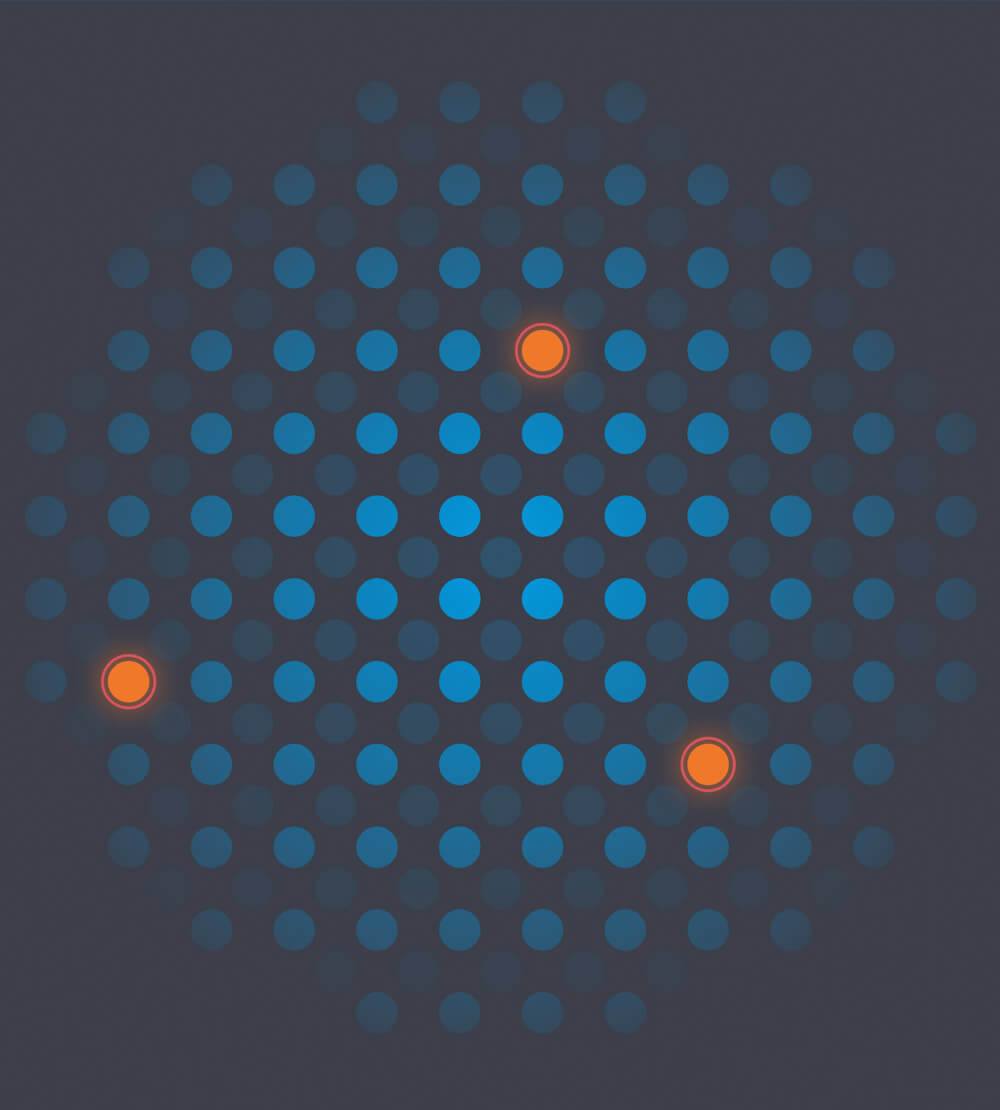
CRITICALSTART uses a trust-oriented approach to handle alerts at scale. Unlike our competitors, we “unprioritize.” In other words, we believe that every security event begins as equal. Our Trusted Behavior Registry (TBR) enables us to put our trust-oriented approach into action by automatically resolving what is known-good and can be safely trusted first – shifting focus to known alerts for triage and quick resolution.

![]()
The CRITICALSTART Difference
The winning combination of these three key pillars makes it possible for CRITICALSTART to resolve alerts quickly and reduce any length of attacker dwell time in your environment.
![]()
Trusted Behavior Registry
Trusted Behavior Registry means we can scale to the needs of your business.
![]()
Full Transparency & Mobility
Full Transparency and Mobility means faster communication and containment of alerts through the convenience of a mobile app.
![]()
The Human Element
The Human Element means we are there around-the-clock, investigating any unknown alerts outside of the Trusted Behavior Registry.

We Leave
Nothing to Chance
The collected knowledge and global learnings of the Trusted Behavior Registry (TBR) playbooks are applied to every customer environment. In mere seconds of deployment, the network effect of the TBR begins working to automatically resolve known-good behaviors, shifting the focus to what matters: The unknown.
Since known-good for an organization isn’t the same for every business, we build on the network effect with adapted playbooks that capture organizational knowledge, tailoring the TBR to meet your business requirements.
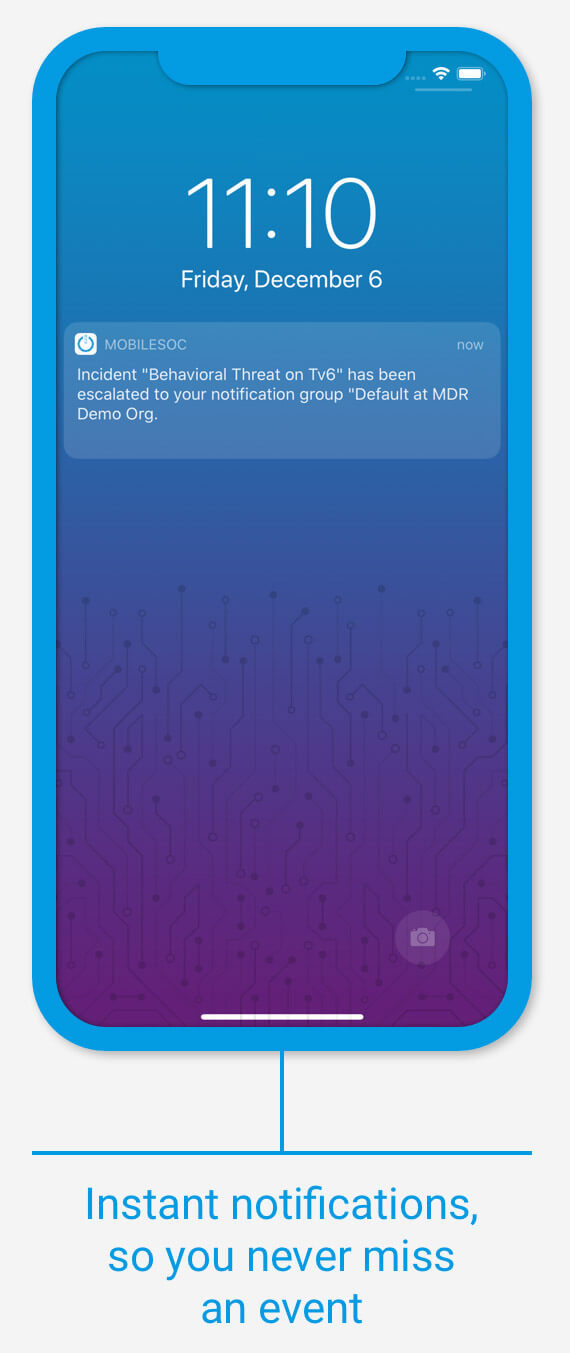
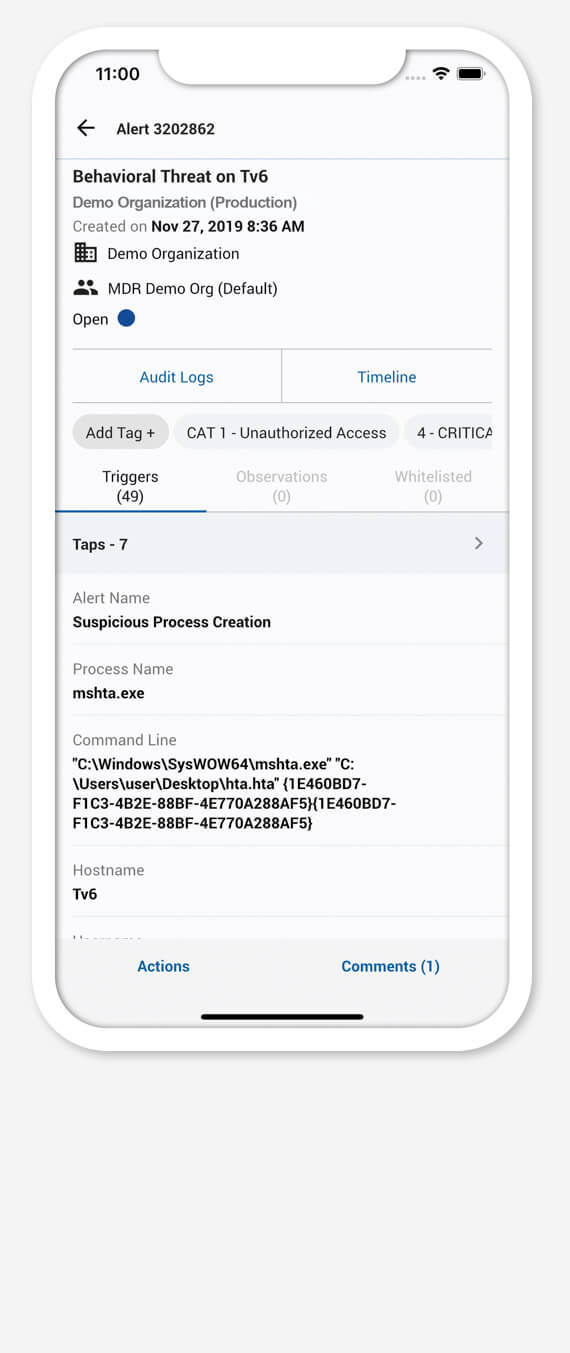
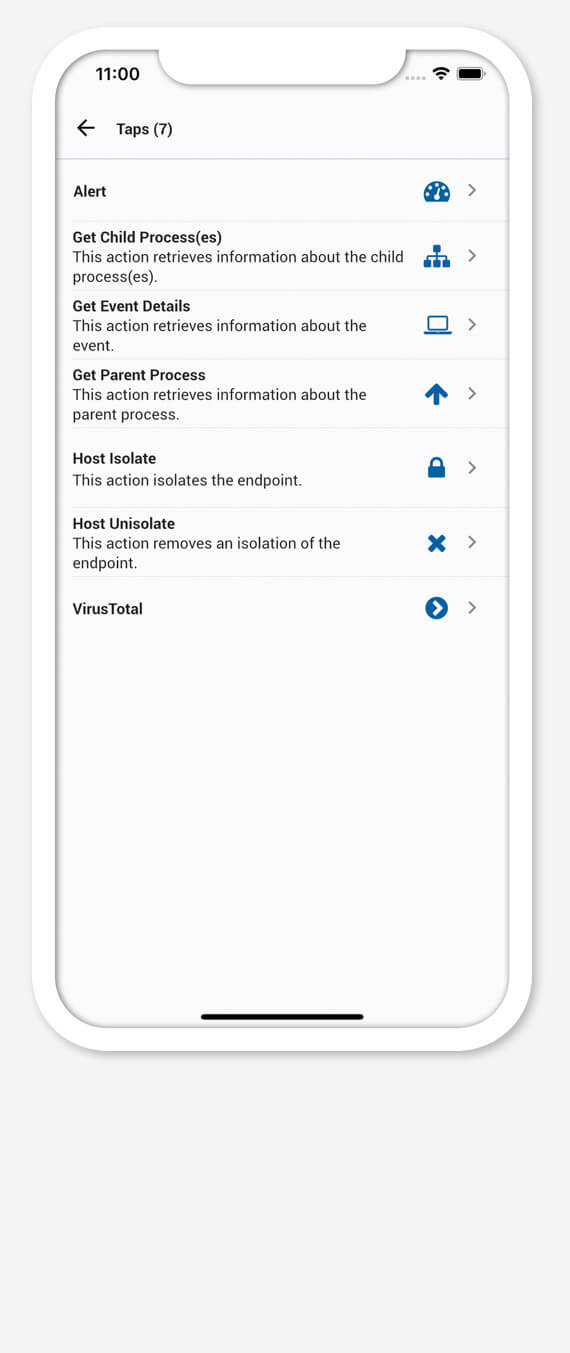
Our MOBILESOC
Drive down attacker dwell time with CRITICALSTART’s MOBILESOC providing remote collaboration, workflow, and response for your SOC. Features include:
![]()
“On-the-Go” Alert Response
Alert Response – Our MOBILESOC can resolve and remediate endpoints
![]()
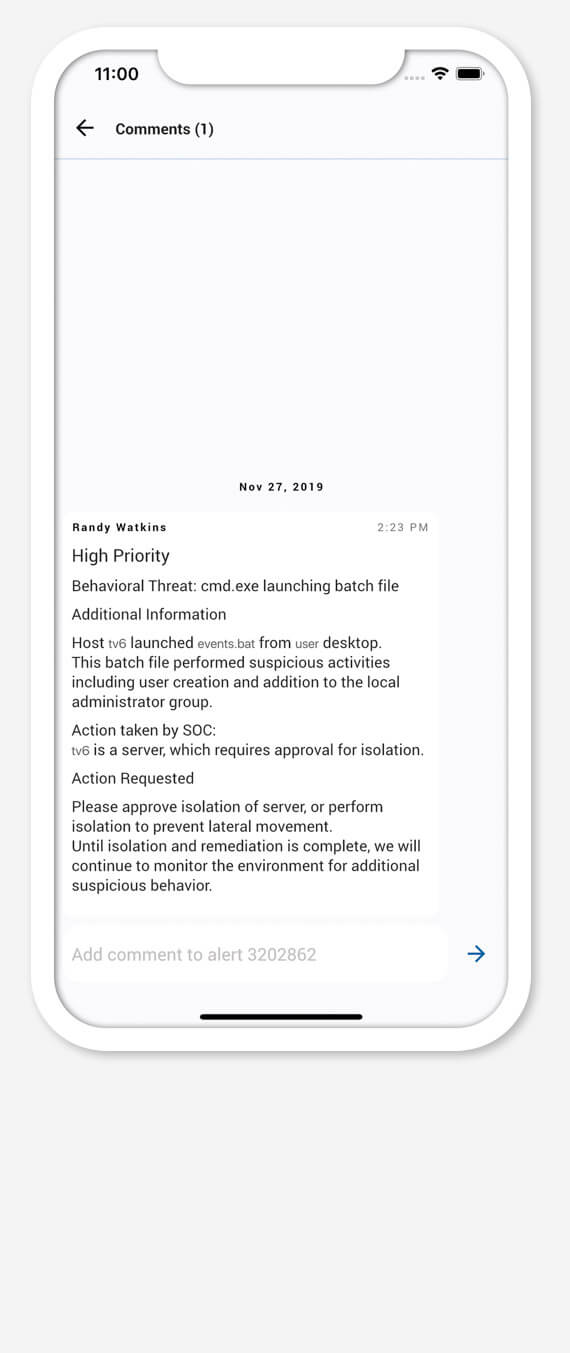
Secure Remote Collaboration
SOC analysts can collaborate remotely with full audit trails.
![]()
Full Access
Protect your users with best-of-breed endpoint prevention.
![]()
Alert Reduction
Access to CRITICALSTART’s Trusted Behavior
Registry increases efficiency of alerts.
![]()
Deploy in Minutes
Fast Deployment via our cloud hosted platform.
![]()
Reduce Dwell Time
The amount of time an attacker is able to operate in your environment. The longer the dwell time, the more likely that an attacker can carry out a breach.