CVE Numbers:
CVE-2018-0437 – Cisco Umbrella ERC releases prior to 2.1.118 and Cisco Umbrella
CVE-2018-0438 – Cisco Umbrella ERC releases prior to 2.1.127
Versions Tested:
Umbrella Roaming Client 2.0.168 […]

CVE Numbers:
CVE-2018-0437 – Cisco Umbrella ERC releases prior to 2.1.118 and Cisco Umbrella
CVE-2018-0438 – Cisco Umbrella ERC releases prior to 2.1.127
Versions Tested:
Umbrella Roaming Client 2.0.168 […]

Security awareness training is broken. Read the news any day of the week and you can find articles talking about breaches, ransomware attacks, and countless records stolen resulting in identity theft victims. Our users are continuing to click suspicious links, open attachments they weren’t expecting, and falling for the call to action. Attackers know that […]
Exploits for network devices including routers, switches, and firewalls have been around for as long as networking has been a thing. It seems like every week a researcher discloses a new vulnerability or publishes proof of concept (PoC) code online for these types of devices, and that is exactly what is happening in this article. […]
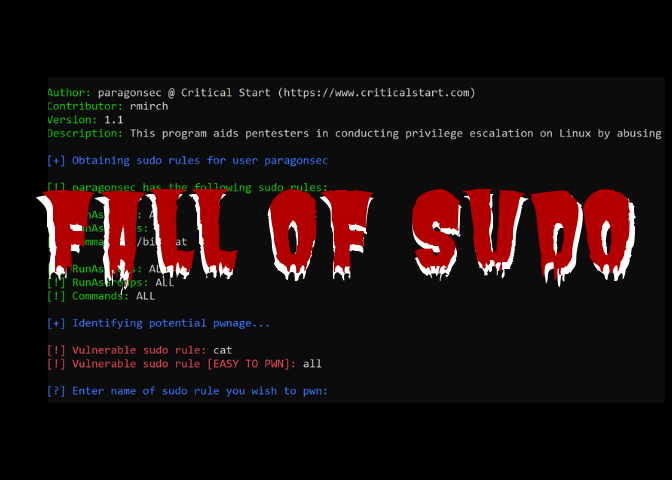
Introduction Finding Linux servers heavily reliant on Sudo rules for daily management tasks is a common occurrence. While not necessarily bad, Sudo rules can quickly become security’s worst nightmare. Before discussing the security implications, let’s first discuss what Sudo is. Defining Sudo What is Sudo? Sudo, which stands for “superuser do!,” is a program […]

In the age of the breach, it’s a safe assumption that almost every public account’s credentials have been exposed at some point. “Have I Been Pwned” (HIBP), is a database that contains usernames and other information about any compromise they come across. While available for individuals to search against, certain protections have been put in […]

An evolution has occurred with the preferred attack method among hackers. With its high potential for a fast return with relatively little right, instances of cryptojacking, the malicious use of a companies’ computer resources to mine for cryptocurrency, have increased 8500% in 2018, according to Symantec. While 2017 saw a rise in ransomware to be […]

You’ve purchased a next-generation firewall. You understand the why, but how do you make the most of your investment? What’s next? When it comes to next-generation firewall technology, determining the best implementation methodology can be a bit daunting. You may ask yourself: What features should I enable first? How do I enable these new capabilities […]

Everyone should be wary of downloading, installing, or running unknown scripts or software (especially from questionable sources on the Internet or unexpected email attachments). The truth is, most of us have been conditioned to be a bit paranoid when running code on our machines, as we should be. This innate distrust of questionable or unknown […]
What’s the big deal? Mathy Vanhoef of imec-DistriNet, KU Leuven has discovered a serious weakness in WPA2, a protocol that secures all modern protected Wi-Fi networks. Vanhoef has released a whitepaper, a video example of an attack, created a thorough website explaining the vulnerability, and will be releasing proof of concept exploit code soon. This […]

The proliferation of wireless devices in the world is astounding, and one of the most widely used are Bluetooth, at an estimated capable device count north of 8 billion. Earlier this week, researchers at Armis released information on their website about an attack vector dubbed “BlueBorne”. The list of vulnerable and exploitable devices spans Android […]
Security Automation and Orchestration (SAO) Platforms are the newest players in the security landscape focusing on easing the burden of alert-fatigue. Working as a lead in a Managed Services Security Operations Center (SOC), solutions that claim to automate actions, lower time-to-response, and minimize required headcount peak my interest. SAOs operate by implementing logical decision trees […]

Today, 27 June 2017, a new malware has begun attacking networks around the world. Petya, also known as Petrwrap, is the name and encrypting your information is its game. It has shown itself to be different than other ransomware of late. This one does not encrypt files one at a time but denies user access […]

Widespread malware affecting media players On May 23rd, 2017, Checkpoint found a vulnerability in four popular media players that use a new attack vector by creating malicious subtitle files to infect computers, smartphones, and smart TVs. Once the files are downloaded, an attacker can potentially take complete control over the device. Over 200 million devices […]

Friday could not have come sooner for some last week. For the rest of us, we may have wished Friday never happened. What is now being considered the most “successful” and prolific ransomware campaign took off like a wildfire in a dry forest. We’ve all heard the name, WannaCry, hopefully, it did not make anyone […]

Technical Details It is currently unclear whether this payload is delivered via malicious attachment or through the WAN using the FuzzBunch EternalBlue SMB exploit. The malware behaves much like typical ransomware during execution on the victim’s machine. Below are the operations that are ran via cmd.exe: /c vssadmin delete shadows /all /quiet & wmic shadowcopy […]
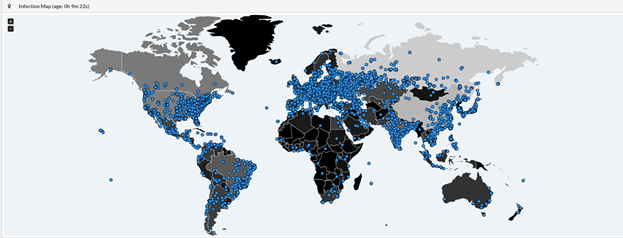
Urgent Information Regarding WanaCrypt/WannaCry/WCry Ransom-ware Outbreak Today, 12 May 2017, a massive ransomware outbreak has been reported across the globe. There are reports of computer systems completely locked up in Russia, Western Europe, East Asia, and North America. British hospitals and a Spanish telecom company have been the largest confirmed victims thus far, along with […]

Adoption of Zero-Trust and Micro-Segmentation as core design principles can help improve the security posture of your network and the attached systems. However, it is important to understand how we got to our current state in order to understand how these principles can help us. Let’s do a quick review of the current network security […]

On Friday, April 14, a group called “Shadow Brokers” released multiple exploits and tools, purported to be from the NSA, entitled “Fifth Leak: Lost in Translation“. Over the holiday weekend, the CRITICALSTART research team and the greater InfoSec community went through and analyzed many of the tools. Affected Systems The tools are primarily comprised […]

Why Security Teams Need a Second Set of Eyes During a recent penetration test, I hijacked the client’s email server, posed as the client CEO, and sent a fraudulent email to the client CFO asking the CFO to wire $10,000 USD to an offshore bank account. Interestingly, after receiving a string of actual malicious phishing […]

I recently conducted a penetration test of a web application. Because of design decisions, I was able to bypass CAPTCHA to brute force user accounts and, ultimately, bypass file upload restrictions to upload malware onto the web server and into the internal network environment. The owner had taken a healthy view of security, had conducted […]

With the current state of cybersecurity, the market has become inundated with “solutions”. When every manufacturer is selling hammers, then all problems look like a nail. Security personnel is expected to evaluate solutions, while still trying to find time for operational tasks. After the media fills executives’ minds with the latest security buzzwords, they all […]
At CRITICALSTART, we use a concept called the Defendable Network and map organizations to SecCon levels designed to give companies a chance against threat actors of varying skill levels. We group threat actors skill levels into: Untrained Attacker (just gets lucky) Novice Attacker Intermediate (using automated tools mostly) Advanced Expert Phineas Fisher is a Blackhat hacker and gave […]